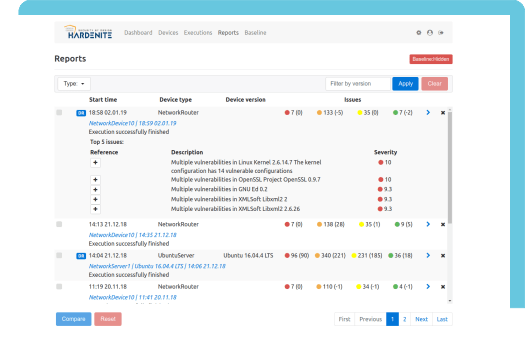
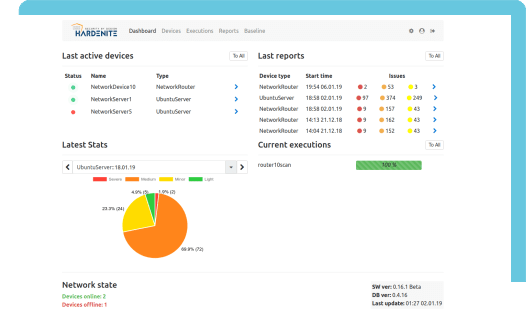
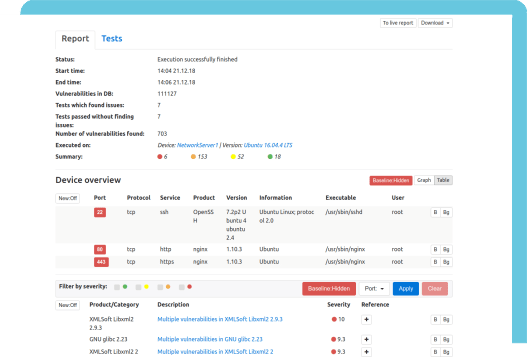
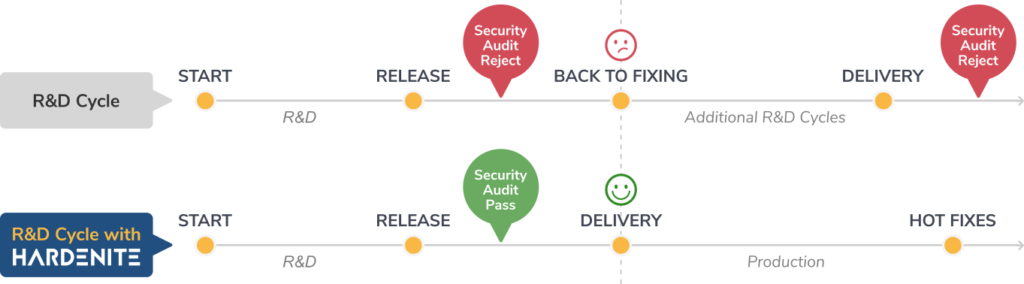
Comprehensive Security auditing for Embedded Software
Implement embedded software security auditing into your development and integration operations: Hardenite Audit is an automatic security audit tool designed to provide complete security management and risk mitigation for products running embedded software, starting with a broad variety of Linux flavors and related open source frameworks.