When choosing a docker container for hosting of your PostgreSQL database, one considerable aspect is how secure your container is, and how much work you will need to invest in order to make it secure. All the open source software coming as part of the container installation brings with it tons of CVEs which need to be addressed as part of the infrastructure hardening.
We decided to compare two popular images used for hosting of PostgreSQL 12.3 in docker: postrges:latest and postgres:alpine. We used Hardenite Audit to analyse images and here are the results:
postrges:latest scan results:
![]()
vs postgres:alpine:
![]()
So the results are clear: thin software layer approach taken by Alpine Linux distribution is proving itself when talking about potential exposure to the known security vulnerabilities.
Let’s now drill down a bit to see what critical issues are still present in the Alpine docker for PostgreSQL 12.3.
There’s only one critical CVE in Busybox 1.31.1: CVE-2018-1000500
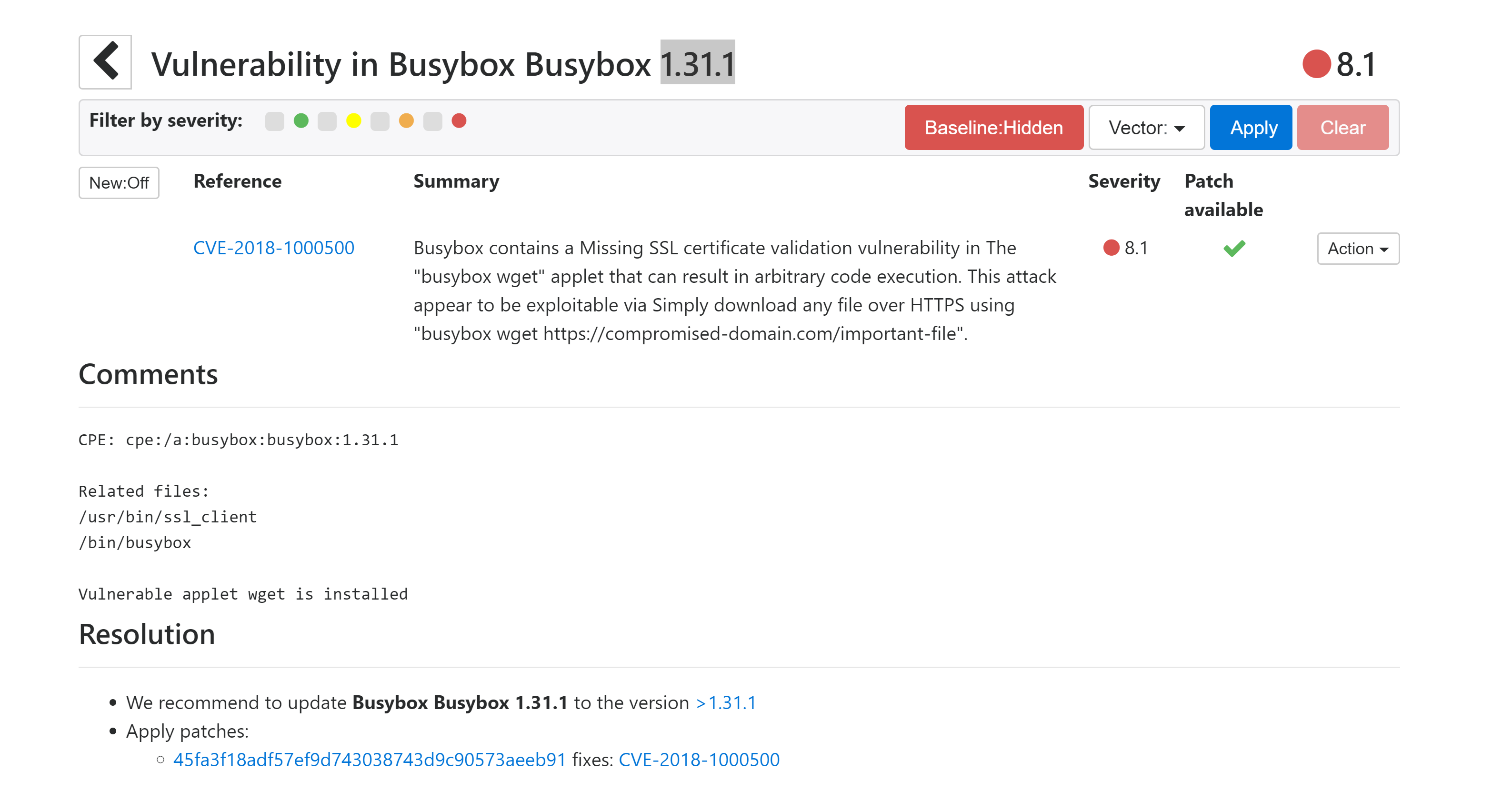
While being a major issue, it doesn’t look like this CVE imposes an immediate risk on the container used to run PostgreSQL.
Conclusion: Alpine container is clearly a good choice from security perspective, when choosing a PostgreSQL docker image.